Cyber Crime Syndicates: The Sobering Truth
These days, there are challenging conversations being had between MSP’s and their customers when it comes to cyber security, cyber insurance, and compliance. On one side, responsible MSP’s are doing everything they can to inform their customers and prospects of the very real risks to their businesses and livelihoods. On the customer side, business owners and executives are struggling to understand what’s really going on, what the real risks are, and are tired of feeling brow beaten into spending time, money, and resources on cyber security. So, what really is going on and what does it mean for you and your business?
Most MSP’s are keenly aware of what’s going on in the “real world” of cybercrime and the risks for each and every business. We have a front row seat to the heavyweight bout that is occurring between organized cyber security crime entities (hackers) and the companies that are doing everything they can to support MSP’s and enterprise IT departments with the tools and services they need to keep up the good fight. The unfortunate truth is that the good guys are always behind, but there are three key things that you should do immediately so that you’re not an easy victim. Implementing key cyber security fundamentals has become essential. We’ll get more into that a bit later in this article.
The first thing you need to come to terms with is that you are a target. Every business is. The bad guys are constantly on the attack. Their mission in this heavyweight fight is to land effective punches that will ultimately result in a knockout blow that forces you to pay large sums of cash to get out of the ring alive. But hackers don’t care about weight class or going after just the big fishes – they’ll take an easy opponent if they’re easy to knock out. And they know, the worse they make it for you, the more you will pay. In our world, we see breaches every single day and we don’t want it to happen to you. You are not immune. If you play Russian roulette for long enough, the odds are not in your favor. For us, it resembles warning our friends and loved ones of the dangers of doing drugs. They cannot have the “it can’t or won’t happen to me” attitude. We all know it only takes once. There are haunting similarities with cyber security, and, yes, lives really are at stake here.
Let’s take a sobering look at what these organizations truly look like. In some ways the MSP industry is doing itself a disservice by portraying these hackers as stereotypical “bad guys” that are loosely organized and either operating out of their parents’ basement, or a secret underground lair in Eastern Europe. Aspects of these stereotypes are true, but the reality of how well structured and organized they are is not conveyed strongly enough. And if that doesn’t scare you, your own employees could be influenced by bribes and payments to assist these bad guys as internal perpetrators.
Let’s start by looking at the different types of cyber threat actors that are out there, and what their motives are:
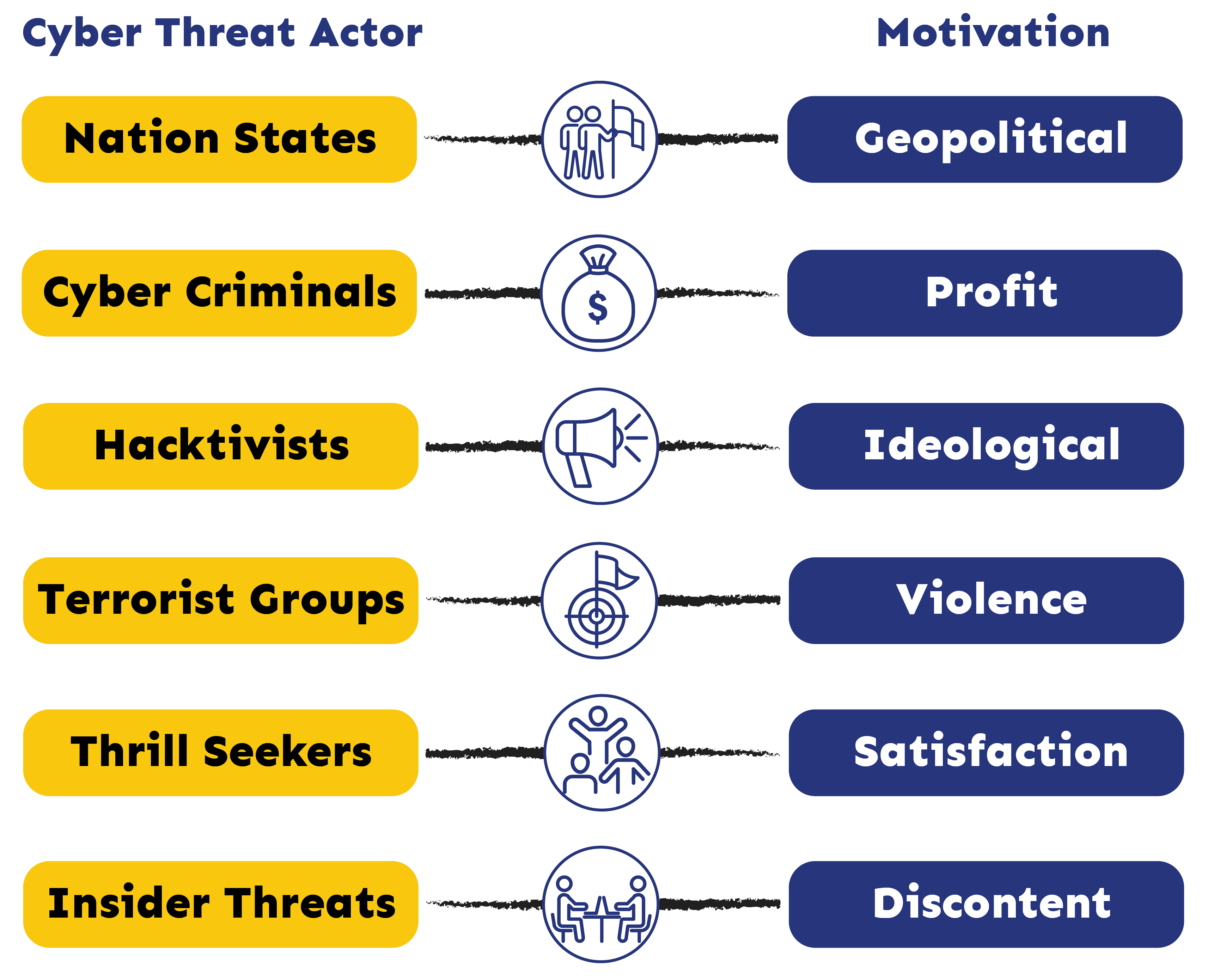
As you can see, there’s a breadth of organizations and motivations. The two primary threat actors that apply to the majority of business sector are cyber criminals and insider threats.
On a global scale cybercrime will cost an estimated $10.5 trillion annually by 2025. Simply put, cybercrime is a huge business and ranks as the world’s third largest economy behind the Unites States and China according to the World Economic Forum.
The first malicious hackers had motives beyond money, notably individual fame and political activism (Anonymous may be the most famous current example). Today, cyber crime syndicates are well organized, structured, white-crime organizations with long term strategies and goals. They recruit and hire positions within specialized career fields just like main-stream, legal organizations.
To better understand this, lets look at some of the key roles these organizations employ to support their supply chain.
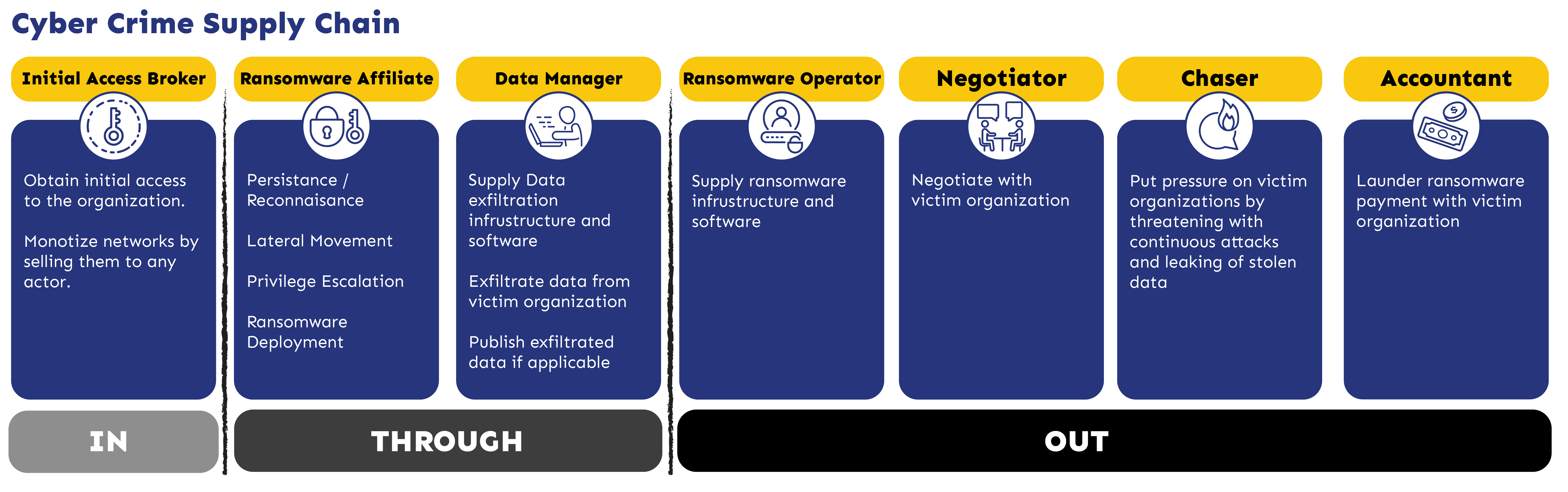
As you can see, these are sophisticated organizations that are generating millions of dollars in profits. The Initial Access Brokers alone are big business. These are the people that are trying to trick you and your staff to give up your precious credentials. Their job and mission are to outsmart you. They utilize legitimate business software and/or existing functions and capabilities within operating systems and applications for their exploits. It is truly a cat and mouse game.
Once they gain access to a network, they typically lie in wait (this is called persistence in the cyber security world) and spread their footprint as far and wide as possible. This is where the Ransomware Affiliates come in and spread laterally through networks. This means getting into your file shares, your backups, your email, and your confidential or sensitive data. Anything and everything they can get into. They do this so that they can hit the nuclear button at some point in the future and cause as much damage as possible. Remember, the more havoc they wreak, the more you will pay.
For some organizations, a natural reaction is to say “I don’t have any sensitive data. What would my data be worth to them?” This is a huge mistake and a naïve statement. My retort would be, “do you have customers? Do you produce anything for those customers or deliver a service to them? What would happen to your business if you couldn’t meet those obligations for days, weeks or months? Would your customers go somewhere else (the answer is always yes even if you think it’s not)? What would that do to your business? If all the data you have for your customers was released to the public, would that have a negative effect on your business and/or reputation?” This is why this applies to every business or entity on earth. Everything from school districts to police departments, to privately owned businesses of all kinds.
Further up the supply chain are the people that extricate data from organizations. The standard tactic is now shifting from encrypting data to flat out deleting it. There’s a couple of reasons why they do this. First, they don’t have to deal with the hassle of providing and supporting decryption keys when a ransom is paid. It also allows them to implement a double-extortion strategy where they threaten to publicly release your data if the ransom is not paid.
They employ negotiators, chasers and accountants to launder money. It may be shocking to hear, but the good-guy cyber incident recovery companies hired by insurance companies are so used to working with these criminal organizations that they have business reputations. When speaking about one such criminal organization, a cyber security analyst once said to me “yeah, those guys have a decent reputation with us and the FBI. When you pay, they’re pretty good at releasing the data quickly and they offer great technical support if you have a problem.” Let that sink in for a minute. They offer great technical support!
Also keep in mind that not all bad actors are always outside of your organization. Insider threats is a real issue. This is where employees are bribed and leveraged to provide access to a network.
So what can you do about all of this? I have a threefold recommendation as the minimum starting point for any business:
- Implement multi-factor authentication everywhere you possibly can. Meaning, if it’s available for any application, website, or service you should enable it and require it. This is not an optional inconvenience any longer. It’s a basic requirement.
- Qualify for cyber insurance at an sufficient coverage amount for your company make sure you stay qualified. This will be the subject of a future article, but you should know that qualifying to get it and carrying an active policy isn’t enough. If you can’t prove that you had the required measures in place at the time of an attack and a claim, your claim will be denied.
- Invest in a cyber security awareness program to continuously train yourself and your staff and require and monitor completion of the training regularly (yes, that means you too). Exercising diligence for cyber security is a habit and behavior that requires constant education and reinforcement. People remain the single most vulnerable attack vector of any breach.
These three items are the tip of the iceberg. There are many other things to consider and cyber security fundamentals and hygiene to put in place. If you’d like to have a conversation about anything covered in this article, please reach out to us. We’re here to help.

