SisAdmin is the Outsourced IT Management choice for businesses with 25+ employees running on the Microsoft Business Stack in King and Snohomish Counties.
Customer Testimonials

Not all outsourced IT options are equal.
Most IT service providers make big promises but fall short on both expertise and service delivery. We are committed to keeping things simple, providing all the IT care you need while delivering world-class customer service.
Boost Your Business with SisAdmin IT Managed Services
SisAdmin is not just a Help Desk; our team aligns your technology to your business goals. This allows you to utilize our full-stack team of professionals to keep your company secure and up-to-date.
They’re pretty cool people too.
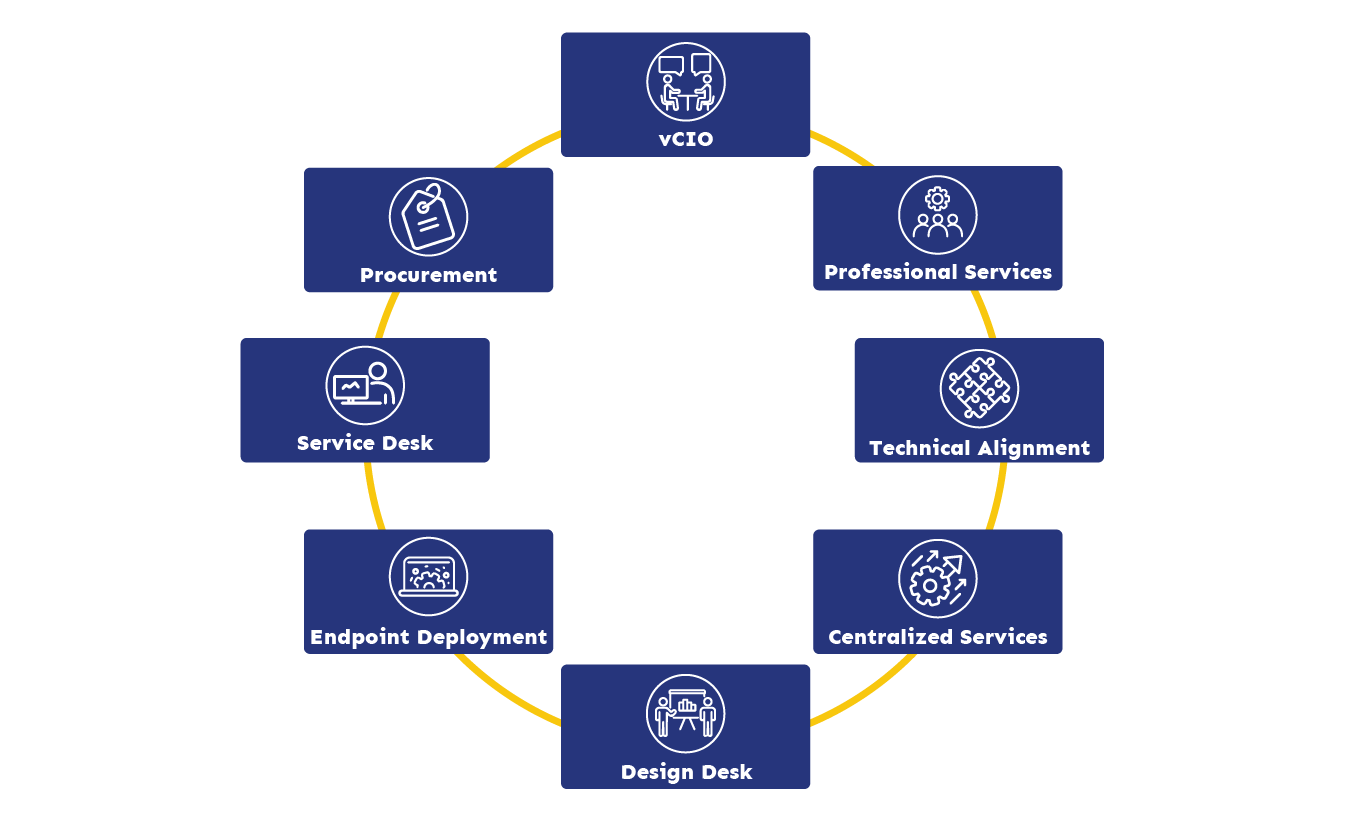
Proactive, Thoughtful Support with SisAdmin Outsourced IT
Realistic promises backed by 20 years of experience providing excellent service.
Continuous real-time alignment heads off issues before they become problems.
One simple plan with a fixed monthly fee that covers all your needs.
Our certified expert team implements protocols that prevent downtime.
Move your IT from a security liability to an operational asset.
Safeguard Your Business with SisAdmin Outsourced IT
Our certified method secures your network from threats as we protect your business and educates your team.
Continuous audits and alignment reduces the need for ticket requests and streamlines your profits.
Our team aligns your technology to your business goals. Plus, they’re nice humans.
C-Suite level management, education, and strategic initiatives for continuous improvement.

Outsourced IT Buying Guide
Make an informed buying choice with the help of our FREE guidebook.
We’ve created this FREE educational resource to explain the different types of provider service plans, clearly define industry terms, and assist you in deciding the best solution for your business.
Download the guide now and gain critical insights when planning your next Outsourced IT Management move!



